What makes Lokey a true random number generator (TRNG)?
Lokey uses a dedicated hardware secure element to produce true entropy.

Most “random” numbers on your systems come from algorithms that can, in principle, be predicted. Lokey streams true hardware randomness from physical noise through an open-source TRaaS API, so your cryptographic keys, AI models, and critical systems start from real unpredictability.
Open source, EU-hosted, no cookies or trackers — verifiable randomness for mission-critical systems.
We publish test reports, run without trackers, and keep every line of code open so your team can verify our randomness.
Dieharder statistical tests passed
View full results →
Cookies or trackers used
Privacy-first by design
Open-source codebase
No black boxes, community-audited
Computers default to pseudo-random number generators (PRNGs)—algorithms that look chaotic but are fully determined by a seed. If an attacker predicts or steals that seed, every subsequent “random” value becomes predictable. True randomness instead comes from messy physical processes, like electronic noise, that have no underlying pattern. For cryptography, secure communications, regulated AI workloads, or national infrastructure, that difference matters. As quantum computing advances, purely algorithmic randomness becomes even easier to exploit, while physics-based entropy stays resistant.
Lokey is an open-source foundation for True Randomness as a Service (TRaaS). We democratize access to hardware-generated entropy with transparent code, published test data, and commercial support only where it adds value.
We deliver value-added services around open hardware and software: managed entropy devices, TRaaS endpoints, compliance support, and custom integrations for high-stakes customers.
Microchip’s ATECC608B amplifies microscopic thermal noise—tiny electrical fluctuations that are fundamentally unpredictable.
Our lightweight firmware and health tests continuously monitor the entropy stream, catching bias or hardware faults in real time.
We feed the raw bits into Fortuna, the robust RNG architecture by Bruce Schneier and Niels Ferguson, to harden output against attacks.
Entropy streams are exposed via API endpoints, CLI tooling, and on-device services—alongside published Dieharder scores and visual analyses for verification.
Four sectors already rely on true randomness to remove single points of failure in cryptography, compliance, and AI. Expand each card to see the workflows Lokey secures.
Integrity and verifiability are non-negotiable for digital services such as identity, voting, notarization, and public lotteries. Lokey provides auditable entropy sources so every key, token, or draw can be challenged and verified.
Financial infrastructure needs defensible randomness for transaction IDs, one-time passwords, customer onboarding, and secure device provisioning. Lokey adds hardware entropy without ripping out existing HSMs.
With multi-tenant environments under regulatory pressure, cloud platforms need hardware randomness to isolate customers, encrypt workloads, and issue API credentials that cannot be replayed.
From reproducible research to safety-critical autonomous systems, AI teams depend on good randomness for weight initialization, data shuffling, and privacy-preserving techniques.
Lokey’s output passes 45 out of 46 Dieharder tests—the industry standard battery derived from George Marsaglia’s original suite and the NIST STS. A 1–5% failure rate is expected for a healthy TRNG; we publish full logs for community review.
Read Dieharder reportWe render 512×512 Data Bitmaps, frequency histograms, and autocorrelation plots. Healthy randomness looks like TV static (no patterns), flat histograms (no bias), and near-zero autocorrelation (no repeated structures).
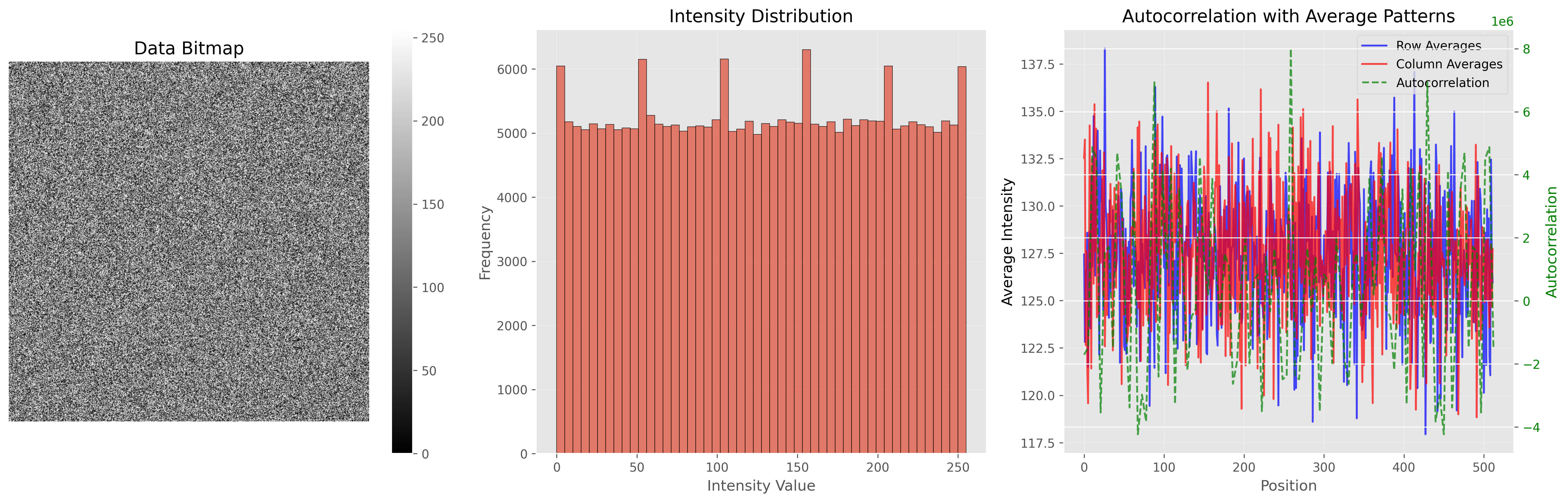
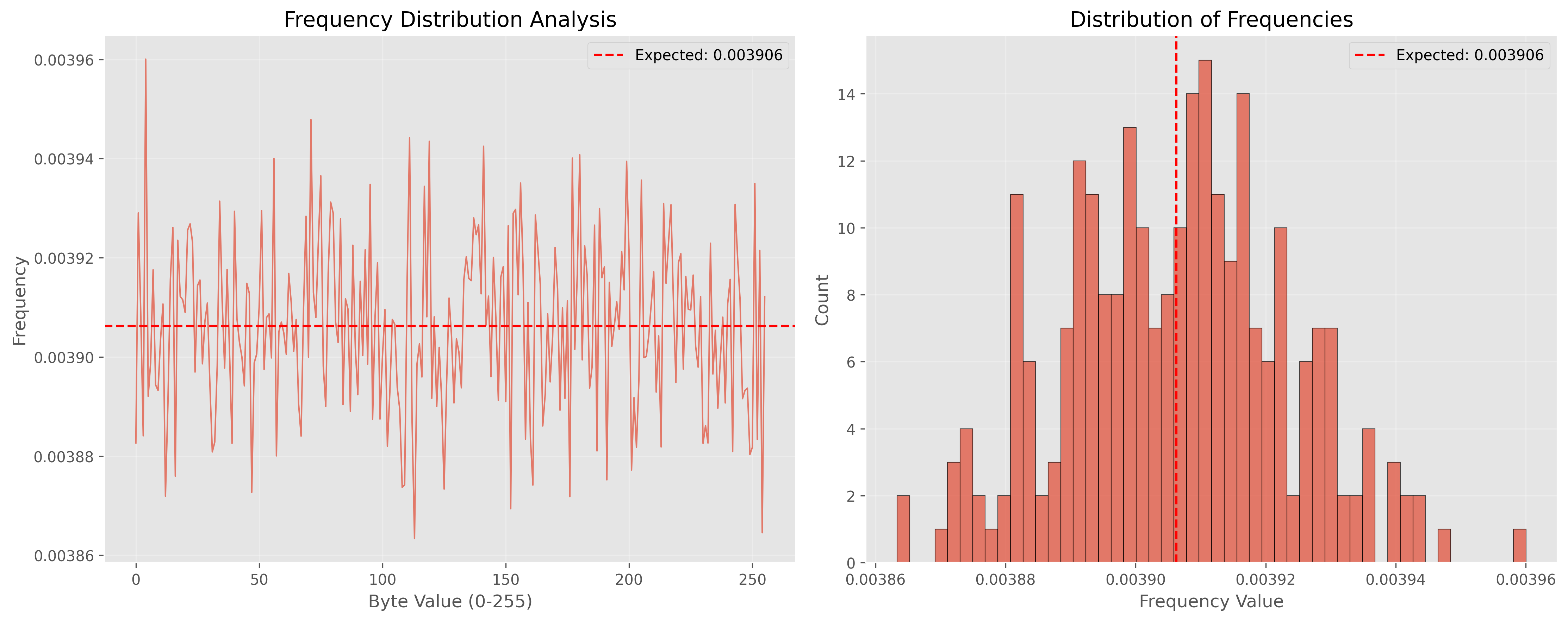
This FAQ covers what we mean by randomness and entropy, how Lokey generates and validates its numbers, and how you can deploy the service inside secure or regulated systems.
Lokey uses a dedicated hardware secure element to produce true entropy.
Hardware entropy provides physical unpredictability unavailable to software PRNGs.
Lokey uses both hardware tests and cryptographic strengthening.
Lokey is designed for self-hosting in strict environments.
Lokey uses industry-standard test suites and visual diagnostics.
Bitmap visualization reveals bias quickly.
Occasional failures are normal; consistent patterns are not.
Lokey is fully open source.
Lokey is developed and operated entirely within the European Union. Your data remains under EU jurisdiction, protected by GDPR and shielded from extraterritorial demands such as the U.S. Patriot Act or CLOUD Act. If regulatory sovereignty matters to you, Lokey keeps your randomness pipeline compliant by default.

Research & Cryptography
Researcher focused on cryptography, algorithms, and Linux—driving Lokey's technical innovation and auditability.

DevOps & Integrations
Runs infrastructure, automation, and third-party integrations—scaling Lokey reliably for enterprise workloads.
We are building an ecosystem around true randomness — and we can’t do it alone. We’re looking for visionary organizations, auditors, and technology integrators to help us define the next-generation randomness infrastructure.